Cybersecurity for Operational Technology: Trends and Tools

As technology advances, Operational Technology (OT) systems are becoming increasingly vulnerable to cyber threats. The convergence of IT and OT systems has created new risks, making cybersecurity a top priority. With the rise of Industrial Internet of Things (IIoT) and connected devices, the attack surface has expanded, putting critical infrastructure and industrial control systems at risk. This article explores the latest trends and tools in cybersecurity for Operational Technology, providing insights into the evolving threat landscape and the measures needed to protect these critical systems. Effective cybersecurity strategies are crucial to prevent disruptions.
Cybersecurity for Operational Technology: Trends and Tools
The increasing use of operational technology (OT) in various industries has led to a growing concern about cybersecurity threats. OT systems, which are used to monitor and control physical devices and processes, are vulnerable to cyber attacks that can have severe consequences on the safety and efficiency of operations. As a result, it is essential to implement effective cybersecurity measures to protect OT systems from these threats. In this context, several trends and tools are emerging to address the unique challenges of OT cybersecurity.
Introduction to Operational Technology Cybersecurity
Operational technology cybersecurity refers to the practices and technologies used to protect OT systems from cyber threats. OT systems are typically used in industries such as manufacturing, energy, and transportation, where they are used to control and monitor physical devices and processes. The cybersecurity of OT systems is critical because a cyber attack on these systems can have severe consequences, including equipment damage, production downtime, and even loss of life. To address these risks, organizations must implement robust cybersecurity measures, such as firewalls, intrusion detection systems, and access control.
Trends in Operational Technology Cybersecurity
Several trends are emerging in OT cybersecurity, including the use of artificial intelligence (AI) and machine learning (ML) to detect and respond to cyber threats. Other trends include the adoption of cloud-based cybersecurity solutions, which can provide scalability and flexibility in protecting OT systems. Additionally, there is a growing focus on incident response and recovery planning, which are critical in minimizing the impact of a cyber attack on OT systems.
Tools for Operational Technology Cybersecurity
A range of tools are available to support OT cybersecurity, including network monitoring tools, vulnerability assessment tools, and incident response tools. These tools can help organizations to detect and respond to cyber threats, as well as to prevent attacks from occurring in the first place. Some examples of OT cybersecurity tools include firewalls, intrusion detection systems, and access control systems.
Benefits of Implementing Operational Technology Cybersecurity
Implementing OT cybersecurity measures can have several benefits, including improved safety, increased efficiency, and reduced costs. By protecting OT systems from cyber threats, organizations can minimize the risk of equipment damage and production downtime, which can have significant financial and reputational consequences. Additionally, OT cybersecurity can help organizations to comply with regulatory requirements and to maintain customer trust.
Challenges in Implementing Operational Technology Cybersecurity
Despite the importance of OT cybersecurity, several challenges can make it difficult to implement effective cybersecurity measures. These challenges include limited resources, lack of expertise, and complexity of OT systems. Additionally, OT systems are often legacy systems, which can make it difficult to implement cybersecurity patches and updates. To address these challenges, organizations must prioritize OT cybersecurity and invest in the necessary tools and expertise.
| Cybersecurity Measure | Description | Benefits |
|---|---|---|
| Firewalls | Network security system that monitors and controls incoming and outgoing network traffic | Prevents unauthorized access to OT systems, reduces risk of cyber attacks |
| Intrusion Detection Systems | System that monitors network traffic for signs of unauthorized access or malicious activity | Detects and alerts on potential cyber threats, enables rapid response and mitigation |
| Access Control Systems | System that controls and manages access to OT systems and networks | Ensures only authorized personnel have access to OT systems, reduces risk of insider threats |
What is operational technology in cyber security?

Operational technology (OT) in cyber security refers to the use of hardware and software to control and monitor industrial processes, such as those found in power plants, water treatment facilities, and transportation systems. OT is used to manage and control the physical aspects of these systems, including sensors, actuators, and control systems. The goal of OT is to ensure the safe and efficient operation of these systems, while also protecting them from cyber threats.
What is the role of operational technology in industrial control systems?
The role of OT in industrial control systems is to provide a reliable and secure way to manage and control the physical processes. This includes monitoring sensor data, controlling actuators, and adjusting control systems as needed. OT systems use communication protocols such as Modbus and SCADA to exchange data between devices and systems. Some of the key features of OT in industrial control systems include:
- Real-time monitoring and control of physical processes
- Use of communication protocols to exchange data between devices and systems
- Implementation of security measures to protect against cyber threats
How does operational technology impact cyber security in industrial environments?
The impact of OT on cyber security in industrial environments is significant, as OT systems are often connected to the internet and other networks, making them vulnerable to cyber attacks. OT systems are also often legacy systems, which can make them more difficult to secure. Some of the key ways that OT impacts cyber security in industrial environments include:
- Increased attack surface due to connected devices and systems
- Potential for disruption of physical processes, which can have serious consequences
- Need for specialized security measures, such as firewalls and intrusion detection systems
What are some best practices for securing operational technology systems?
Securing OT systems requires a comprehensive approach that includes technical, operational, and managerial measures. Some best practices for securing OT systems include:
- Implementing strong passwords and access controls to prevent unauthorized access
- Conducting regular vulnerability assessments and penetration testing to identify security weaknesses
- Using segmentation and isolation to limit the attack surface and prevent lateral movement
What are the OT security trends for 2024?
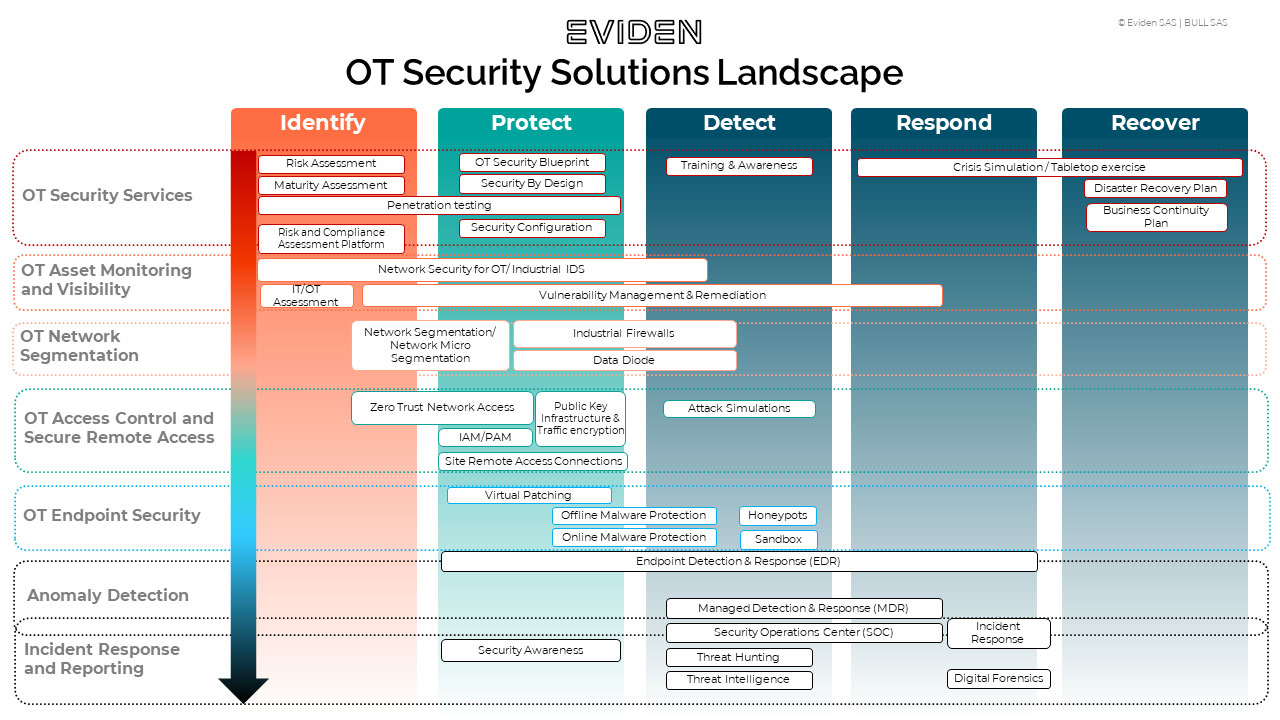
The Operational Technology (OT) security landscape is expected to undergo significant changes in 2024, driven by the increasing connectivity and interoperability of OT systems. As OT systems become more interconnected, the risk of cyber attacks and data breaches also increases, making it essential to stay ahead of emerging threats. The industrial control systems (ICS), supervisory control and data acquisition (SCADA) systems, and other OT systems will require more robust security measures to prevent potential disruptions.
Emerging Threats in OT Security
The OT security landscape in 2024 will be characterized by sophisticated threats, including ransomware and denial-of-service (DoS) attacks. To mitigate these threats, organizations will need to implement advanced security solutions, such as artificial intelligence (AI) and machine learning (ML)-based intrusion detection systems. Some key measures to address emerging threats include:
- Implementing threat intelligence platforms to stay informed about potential threats
- Conducting regular vulnerability assessments to identify and address weaknesses
- Developing incident response plans to quickly respond to security incidents
OT Security Best Practices
To ensure the security and reliability of OT systems, organizations will need to adopt best practices, such as network segmentation, access control, and continuous monitoring. By implementing these measures, organizations can reduce the risk of cyber attacks and data breaches, and ensure the availability and integrity of their OT systems. Some key best practices include:
- Implementing role-based access control to restrict access to authorized personnel
- Conducting regular security audits to identify and address vulnerabilities
- Developing security awareness training programs to educate employees about OT security risks
Convergence of IT and OT Security
The convergence of Information Technology (IT) and OT security will be a significant trend in 2024, as organizations recognize the need for a unified security approach. By integrating IT and OT security, organizations can leverage shared resources and expertise to improve the overall security posture of their OT systems. Some key benefits of IT-OT convergence include:
- Improved incident response through shared threat intelligence and incident response plans
- Enhanced security visibility through unified security monitoring and analytics
- Reduced security costs through shared security resources and economies of scale
What are the trends in operational technology?
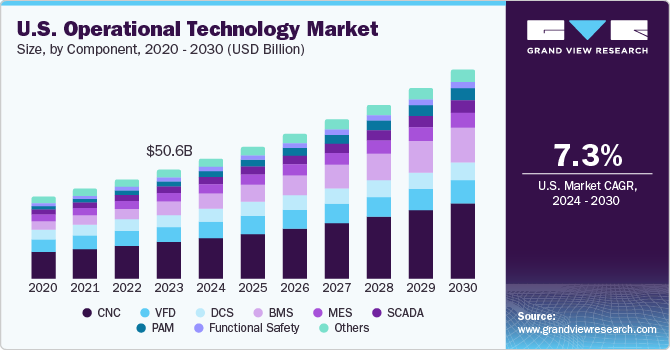
The trends in operational technology are shaping the way industries operate and manage their systems. One of the key trends is the increasing use of Internet of Things (IoT) devices, which enable real-time monitoring and control of equipment and processes. This has led to improved efficiency and productivity in various sectors, including manufacturing, oil and gas, and transportation.
Advances in Automation
The trend towards automation is driving the adoption of artificial intelligence (AI) and machine learning (ML) in operational technology. This enables systems to learn from data and make predictive maintenance decisions, reducing downtime and improving overall system reliability. Some key aspects of advances in automation include:
- Increased use of robotics to perform repetitive and hazardous tasks
- Implementation of AI-powered control systems to optimize process control and improve safety
- Development of autonomous systems that can operate independently with minimal human intervention
Cybersecurity in Operational Technology
As operational technology becomes more connected, the risk of cyberattacks increases. Therefore, cybersecurity is becoming a major concern in this field. The trend is towards implementing robust security measures to protect against malware and ransomware attacks. Some key aspects of cybersecurity in operational technology include:
- Implementation of firewalls and intrusion detection systems to prevent unauthorized access
- Use of encryption to protect sensitive data and prevent data breaches
- Regular security audits and penetration testing to identify vulnerabilities and improve incident response
Data Analytics in Operational Technology
The increasing amount of data generated by operational technology systems is driving the trend towards data analytics. This enables organizations to gain valuable insights into their operations and make data-driven decisions. Some key aspects of data analytics in operational technology include:
- Use of big data analytics to identify trends and patterns in system performance
- Implementation of predictive analytics to forecast equipment failures and reduce downtime
- Development of digital twins to simulate system behavior and optimize performance
What are the top 3 cyber security trends?

The top 3 cyber security trends are shaped by the evolving nature of threats and the development of new technologies to counter them. As the cyber landscape continues to change, cybersecurity measures must adapt to protect against new and emerging threats. The trends are influenced by factors such as the increase in remote work, the Internet of Things (IoT), and the sophistication of cyberattacks.
Cybersecurity Threats Evolution
The evolution of cybersecurity threats is a significant trend. This includes the rise of ransomware, phishing, and social engineering attacks. These threats are becoming more sophisticated, making them harder to detect and defend against. Some key developments in this area include:
- The use of artificial intelligence (AI) and machine learning (ML) by attackers to create more effective and targeted attacks.
- The exploitation of vulnerabilities in software and hardware to gain unauthorized access to systems.
- The increase in distributed denial-of-service (DDoS) attacks that can overwhelm a network with traffic from multiple sources.
Advancements in Cybersecurity Technologies
Advancements in cybersecurity technologies are another critical trend. This encompasses the development and implementation of security solutions such as cloud security, endpoint security, and network security. These technologies are designed to protect against various types of cyber threats. Some notable advancements include:
- The implementation of zero-trust architecture, which requires strict verification for all users and devices, regardless of whether they are inside or outside the network.
- The use of encryption to protect data both at rest and in transit, making it unreadable to unauthorized parties.
- The deployment of security information and event management (SIEM) systems to monitor and analyze security-related data from various sources.
Importance of Cybersecurity Awareness and Training
The importance of cybersecurity awareness and training cannot be overstated. As cyber threats continue to evolve, it is crucial that individuals understand how to protect themselves and their organizations from these threats. This includes being aware of best practices for password management, recognizing phishing emails, and understanding the risks associated with using public Wi-Fi. Key aspects of cybersecurity awareness and training include:
- Regular training sessions for employees to educate them on the latest cyber threats and how to defend against them.
- Simulated phishing attacks to test employees' awareness and preparedness.
- Incident response planning to ensure that organizations are ready to respond effectively in the event of a cybersecurity incident.
Frequently Asked Questions
What are the current trends in Cybersecurity for Operational Technology?
The current trends in Cybersecurity for Operational Technology are focused on protecting Industrial Control Systems (ICS) and Supervisory Control and Data Acquisition (SCADA) systems from cyber threats. This includes the use of artificial intelligence (AI) and machine learning (ML) to detect and respond to anomalies in real-time. Another trend is the adoption of cloud-based security solutions to provide scalability and flexibility in securing operational technology (OT) systems. Additionally, there is a growing emphasis on incident response planning and cybersecurity training for OT personnel to ensure they are equipped to handle cybersecurity incidents. The use of threat intelligence and vulnerability management are also becoming increasingly important in identifying and mitigating potential threats to OT systems.
What are the most effective tools for securing Operational Technology systems?
The most effective tools for securing Operational Technology (OT) systems include firewalls, intrusion detection systems (IDS), and intrusion prevention systems (IPS) to protect against unauthorized access and malicious activity. Encryption and secure authentication protocols, such as SSL/TLS and Kerberos, are also essential for protecting data in transit and ensuring secure access to OT systems. Network segmentation and access control are also critical in limiting the attack surface and preventing lateral movement in case of a breach. Furthermore, security information and event management (SIEM) systems are used to monitor and analyze security-related data from various OT systems to detect and respond to security incidents. The use of industrial control system (ICS)-specific security tools, such as ICS-specific firewalls and ICS-specific intrusion detection systems, is also becoming increasingly important.
How does the convergence of IT and OT systems impact Cybersecurity?
The convergence of IT and OT systems has significant implications for Cybersecurity. As IT and OT systems become more interconnected, the attack surface increases, and cyber threats can more easily spread from IT systems to OT systems. This requires IT and OT teams to work together to implement integrated cybersecurity solutions that address the unique security requirements of both IT and OT systems. The use of common security protocols and standards, such as NIST Cybersecurity Framework, can help to ensure consistent security practices across IT and OT systems. Additionally, the convergence of IT and OT systems requires increased visibility and monitoring of OT systems to detect and respond to cybersecurity incidents in real-time. The use of industrial control system (ICS)-specific security tools and technologies, such as ICS-specific network monitoring, is also essential in protecting OT systems from cyber threats.
What are the key challenges in implementing effective Cybersecurity for Operational Technology?
The key challenges in implementing effective Cybersecurity for Operational Technology include limited resources, lack of cybersecurity expertise, and complexity of OT systems. Additionally, OT systems often have limited visibility and monitoring, making it difficult to detect and respond to cybersecurity incidents. The use of legacy systems and outdated technologies can also create vulnerabilities that can be exploited by cyber attackers. Furthermore, the convergence of IT and OT systems can create integration challenges, and the lack of standardization in OT systems can make it difficult to implement consistent security practices. The need for continuous monitoring and incident response planning can also be a challenge, as OT systems often require 24/7 operation and minimal downtime. To overcome these challenges, organizations must prioritize cybersecurity and invest in cybersecurity solutions and expertise specifically designed for OT systems.
Leave a Reply