How IBM Guardium Ensures Enterprise Data Security
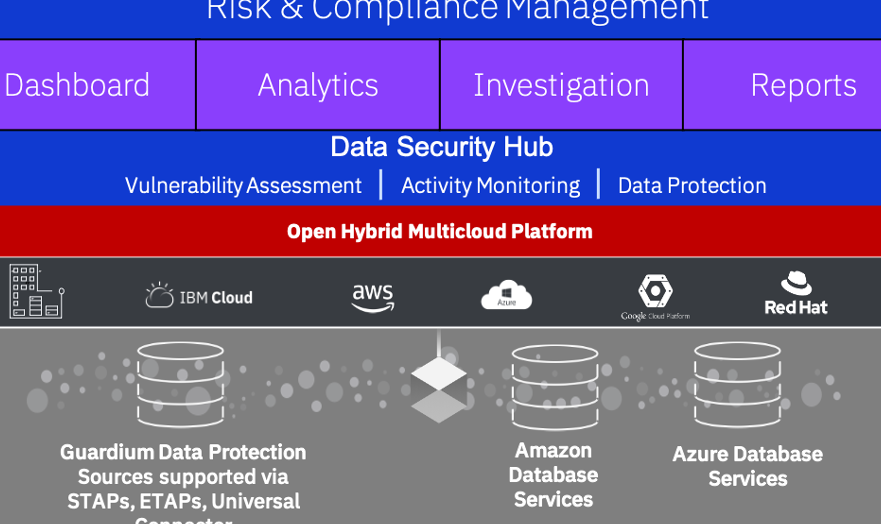
Enterprise data security is a top priority for organizations, as sensitive information is constantly at risk of being compromised. With the rise of cyber threats and data breaches, companies must invest in robust security solutions to protect their assets. IBM Guardium is a leading data security platform designed to help enterprises safeguard their sensitive data. By providing real-time monitoring, encryption, and access control, Guardium ensures that sensitive information is secure and compliant with regulatory requirements, giving organizations peace of mind and protecting their reputation. Effective data security is crucial for business success and continuity.
Ensuring Enterprise Data Security with IBM Guardium
IBM Guardium is a comprehensive data security platform that provides a robust and scalable solution for protecting enterprise data. With its advanced features and capabilities, IBM Guardium helps organizations to safeguard their sensitive data from cyber threats, data breaches, and unauthorized access. In this article, we will explore how IBM Guardium ensures enterprise data security and its key features.
Real-Time Monitoring and Alerts
IBM Guardium provides real-time monitoring and alerts to help organizations detect and respond to potential security threats. Its advanced monitoring capabilities allow administrators to track all database activity, including read, write, and delete operations. With its alert system, administrators can receive notifications when suspicious activity is detected, enabling them to take prompt action to prevent data breaches.
Data Encryption and Masking
IBM Guardium provides data encryption and masking capabilities to protect sensitive data from unauthorized access. Its encryption features ensure that data is protected both in transit and at rest, while its masking capabilities hide sensitive data from unauthorized users. This helps to prevent data breaches and ensures that sensitive data is only accessible to authorized personnel.
Access Control and Authentication
IBM Guardium provides robust access control and authentication features to ensure that only authorized users can access sensitive data. Its role-based access control capabilities allow administrators to define user roles and permissions, while its authentication features ensure that users are who they claim to be. This helps to prevent unauthorized access and ensures that sensitive data is only accessible to authorized users.
Data Discovery and Classification
IBM Guardium provides data discovery and classification capabilities to help organizations identify and classify sensitive data. Its data discovery features allow administrators to scan databases and identify sensitive data, while its classification capabilities enable administrators to categorize data based on its sensitivity. This helps organizations to understand where their sensitive data is located and to take steps to protect it.
Compliance and Regulatory Support
IBM Guardium provides compliance and regulatory support to help organizations meet regulatory requirements. Its compliance features ensure that organizations can meet data protection regulations, such as GDPR and HIPAA, while its regulatory support capabilities provide guidance on how to comply with regulatory requirements. This helps organizations to avoid fines and penalties associated with non-compliance.
| Feature | Description |
|---|---|
| Real-Time Monitoring | Monitors database activity in real-time |
| Data Encryption | Protects data both in transit and at rest |
| Access Control | Provides role-based access control and authentication |
| Data Discovery | Scans databases to identify sensitive data |
| Compliance Support | Provides guidance on regulatory compliance |
What key activity does Guardium Data Protection monitor?

The key activity that Guardium Data Protection monitors is data access and usage. This includes monitoring and analyzing all access to sensitive data, such as databases, files, and applications, to detect and prevent unauthorized access, malicious activity, and data breaches.
Monitoring Data Access
Guardium Data Protection monitors real-time data access and usage to identify potential security threats. This includes monitoring database queries, file access, and application usage to detect anomalous activity. Some key features of Guardium Data Protection's monitoring capabilities include:
- Real-time monitoring of data access and usage
- Anomaly detection to identify potential security threats
- Alerting and reporting to notify administrators of potential issues
Protecting Sensitive Data
Guardium Data Protection helps protect sensitive data from unauthorized access and malicious activity. This includes monitoring data encryption, access controls, and data masking to ensure that sensitive data is protected. Some key features of Guardium Data Protection's data protection capabilities include:
- Data encryption to protect sensitive data in transit and at rest
- Access controls to restrict access to sensitive data
- Data masking to hide sensitive data from unauthorized users
Compliance and Governance
Guardium Data Protection helps organizations meet compliance and governance requirements by monitoring and reporting on data access and usage. This includes monitoring regulatory compliance, data privacy, and data security to ensure that organizations are meeting their compliance and governance obligations. Some key features of Guardium Data Protection's compliance and governance capabilities include:
- Compliance reporting to help organizations meet regulatory requirements
- Data privacy monitoring to protect sensitive personal data
- Data security monitoring to detect and prevent security threats
How does Guardium work?

Guardium is a comprehensive data security platform that provides real-time monitoring, detection, and prevention of unauthorized data access and exfiltration. It works by deploying a network of sensors and collectors that capture and analyze data activity across the enterprise, including databases, file systems, and networks. This allows organizations to identify and respond to potential security threats in real-time, reducing the risk of data breaches and cyber attacks.
Key Components of Guardium
The key components of Guardium include data monitors, activity trackers, and threat analyzers. These components work together to provide a comprehensive view of data activity and identify potential security threats. Some of the key features of Guardium include:
- Real-time monitoring: Guardium provides real-time monitoring of data activity, allowing organizations to detect and respond to potential security threats as they occur.
- Advanced analytics: Guardium uses advanced analytics and machine learning algorithms to identify patterns and anomalies in data activity, helping to detect potential security threats.
- Automated response: Guardium provides automated response capabilities, allowing organizations to quickly respond to potential security threats and prevent data breaches.
How Guardium Identifies Security Threats
Guardium identifies security threats by analyzing data activity and identifying patterns and anomalies that may indicate a potential security risk. This includes monitoring for unusual login activity, suspicious data access, and anomalous network traffic. Guardium uses a combination of rule-based and behavioral-based analysis to identify potential security threats, allowing organizations to respond quickly and effectively to potential security incidents. Some of the key ways that Guardium identifies security threats include:
- Monitoring database activity: Guardium monitors database activity, including SQL queries, data updates, and user access.
- Analyzing network traffic: Guardium analyzes network traffic, including packets, protocols, and ports.
- Tracking user behavior: Guardium tracks user behavior, including login activity, file access, and system changes.
Benefits of Using Guardium
The benefits of using Guardium include improved security, reduced risk, and increased compliance. By providing real-time monitoring and detection of potential security threats, Guardium helps organizations to prevent data breaches and cyber attacks. Some of the key benefits of using Guardium include:
- Enhanced security posture: Guardium provides a comprehensive view of data activity, allowing organizations to identify and respond to potential security threats.
- Reduced risk of data breaches: Guardium helps to prevent data breaches by detecting and responding to potential security threats in real-time.
- Improved compliance: Guardium helps organizations to meet regulatory requirements and industry standards by providing a comprehensive security solution.
What is the basic value proposition of IBM Security Guardium?

The basic value proposition of IBM Security Guardium is to provide a comprehensive data security and compliance solution that helps organizations protect their sensitive data from unauthorized access, theft, and malicious activities. This is achieved through a combination of data discovery, classification, and protection capabilities, which enable organizations to identify, classify, and secure their sensitive data across various environments, including on-premises, cloud, and hybrid environments.
Key Features of IBM Security Guardium
The key features of IBM Security Guardium include data discovery, data classification, access control, encryption, and compliance management. These features work together to provide a robust security framework that helps organizations protect their sensitive data and meet regulatory requirements. Some of the key benefits of using IBM Security Guardium include:
- Improved data security: Through the use of access control, encryption, and other security measures, IBM Security Guardium helps organizations protect their sensitive data from unauthorized access and theft.
- Simplified compliance management: IBM Security Guardium provides a range of tools and features that help organizations meet regulatory requirements and industry standards, such as GDPR, HIPAA, and PCI-DSS.
- Enhanced data visibility: Through the use of data discovery and classification capabilities, IBM Security Guardium provides organizations with a clear understanding of where their sensitive data is located and how it is being used.
Benefits of Using IBM Security Guardium
The benefits of using IBM Security Guardium include reduced risk, improved compliance, and increased efficiency. By providing a comprehensive data security and compliance solution, IBM Security Guardium helps organizations reduce the risk of data breaches and cyber attacks, while also improving their ability to meet regulatory requirements. Some of the key benefits of using IBM Security Guardium include:
- Reduced risk of data breaches: Through the use of access control, encryption, and other security measures, IBM Security Guardium helps organizations reduce the risk of data breaches and cyber attacks.
- Improved compliance management: IBM Security Guardium provides a range of tools and features that help organizations meet regulatory requirements and industry standards.
- Increased efficiency: By automating many of the tasks associated with data security and compliance, IBM Security Guardium helps organizations increase efficiency and reduce costs.
Use Cases for IBM Security Guardium
IBM Security Guardium can be used in a variety of use cases, including data protection, compliance management, and risk management. Some of the key use cases for IBM Security Guardium include:
- Protecting sensitive data: IBM Security Guardium can be used to protect sensitive data, such as personal identifiable information (PII), financial data, and intellectual property.
- Meeting regulatory requirements: IBM Security Guardium can be used to help organizations meet regulatory requirements, such as GDPR, HIPAA, and PCI-DSS.
- Managing risk: IBM Security Guardium can be used to help organizations manage risk, by providing a comprehensive view of their data security and compliance posture.
What is the Guardium tool used for?
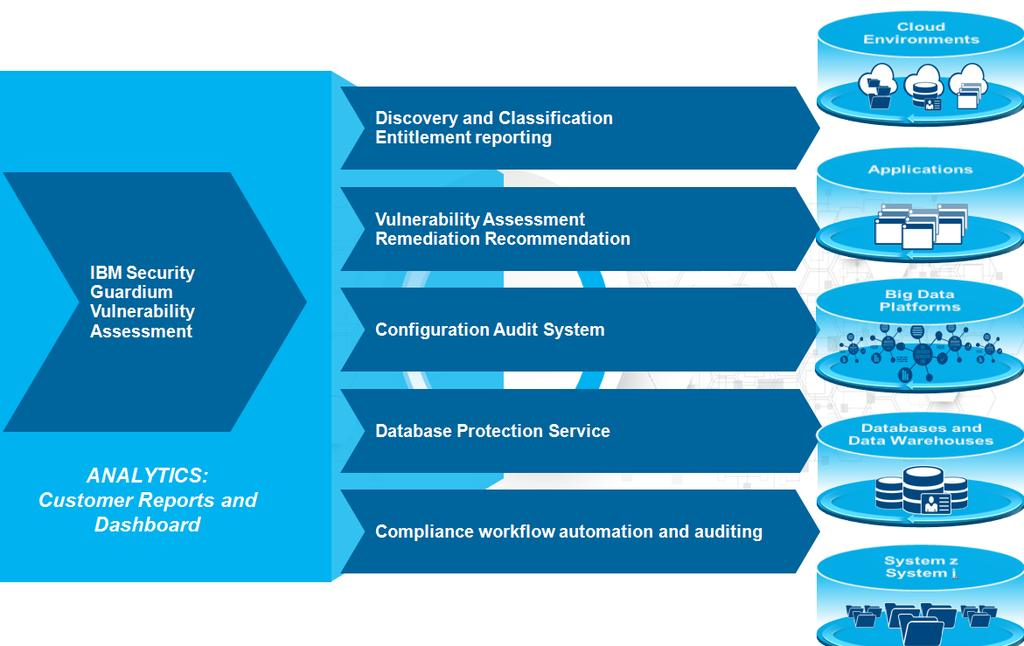
The Guardium tool is used for data security and compliance purposes. It is a comprehensive data protection platform that helps organizations to monitor, analyze, and protect their sensitive data from unauthorized access, theft, or other malicious activities. The tool provides a wide range of features, including real-time monitoring, auditing, and reporting, to help organizations meet regulatory requirements and ensure the integrity and confidentiality of their data.
Key Features of Guardium Tool
The Guardium tool has several key features that make it an effective solution for data security and compliance. Some of the key features include:
- Data Discovery: The tool helps organizations to identify and classify sensitive data across their entire infrastructure, including databases, files, and applications.
- Real-time Monitoring: The tool provides real-time monitoring of data access and usage, allowing organizations to quickly detect and respond to security threats.
- Compliance Reporting: The tool provides pre-built reports and dashboards to help organizations meet regulatory requirements, such as HIPAA, PCI-DSS, and GDPR.
Benefits of Using Guardium Tool
The Guardium tool provides several benefits to organizations, including improved data security, reduced risk, and increased compliance. Some of the benefits include:
- Improved Data Protection: The tool helps organizations to protect their sensitive data from unauthorized access, theft, or other malicious activities.
- Reduced Risk: The tool helps organizations to reduce the risk of data breaches and cyber attacks by providing real-time monitoring and alerts.
- Increased Compliance: The tool helps organizations to meet regulatory requirements and compliance standards, reducing the risk of fines and penalties.
Use Cases for Guardium Tool
The Guardium tool can be used in a variety of use cases, including data security, compliance, and risk management. Some of the use cases include:
- Data Security: The tool can be used to monitor and protect sensitive data from unauthorized access, theft, or other malicious activities.
- Compliance: The tool can be used to meet regulatory requirements and compliance standards, such as HIPAA, PCI-DSS, and GDPR.
- Risk Management: The tool can be used to identify and mitigate risks associated with data breaches and cyber attacks.
Frequently Asked Questions
What is IBM Guardium and How Does it Ensure Data Security?
IBM Guardium is a comprehensive data security and compliance solution that helps enterprises protect their sensitive data from unauthorized access, theft, and corruption. It provides a robust security framework that enables organizations to monitor, detect, and prevent threats in real-time, ensuring the confidentiality, integrity, and availability of their data assets. With IBM Guardium, enterprises can discover, classify, and protect their sensitive data, while also ensuring compliance with regulatory requirements and industry standards. By leveraging advanced analytics and machine learning capabilities, IBM Guardium helps organizations identify and respond to security threats more effectively, reducing the risk of data breaches and cyber attacks.
How Does IBM Guardium Monitor and Protect Sensitive Data?
IBM Guardium provides a range of monitoring and protection capabilities to help enterprises safeguard their sensitive data. It includes real-time monitoring of database activity, file activity, and network traffic, enabling organizations to quickly identify and respond to security threats. Additionally, IBM Guardium offers data masking, data encryption, and access control features to protect sensitive data from unauthorized access. The solution also provides auditing and logging capabilities to help organizations track and analyze security events, ensuring that they can detect and respond to security incidents more effectively. By leveraging these capabilities, enterprises can ensure that their sensitive data is secure and compliant with regulatory requirements.
What are the Key Benefits of Using IBM Guardium for Enterprise Data Security?
The key benefits of using IBM Guardium for enterprise data security include improved security posture, reduced risk of data breaches, and enhanced compliance with regulatory requirements. IBM Guardium helps organizations protect their sensitive data from unauthorized access, theft, and corruption, while also ensuring that they can detect and respond to security threats more effectively. The solution also provides real-time monitoring and analytics capabilities, enabling organizations to quickly identify and respond to security incidents. Furthermore, IBM Guardium helps enterprises streamline their security operations, reduce security costs, and improve their overall security efficiency. By leveraging these benefits, organizations can ensure that their sensitive data is secure, compliant, and available to authorized users.
How Does IBM Guardium Support Compliance with Regulatory Requirements?
IBM Guardium provides a range of compliance features to help enterprises meet regulatory requirements and industry standards. The solution includes pre-built compliance templates and reporting capabilities to help organizations demonstrate compliance with regulations such as GDPR, HIPAA, and PCI-DSS. Additionally, IBM Guardium offers auditing and logging capabilities to help organizations track and analyze security events, ensuring that they can detect and respond to security incidents more effectively. The solution also provides data discovery and classification capabilities to help organizations identify and protect sensitive data, while also ensuring that they can demonstrate compliance with regulatory requirements. By leveraging these capabilities, enterprises can ensure that their sensitive data is secure, compliant, and available to authorized users, while also reducing the risk of non-compliance and regulatory penalties.
Leave a Reply