OT vs. IT Security: Key Differences and Best Practices
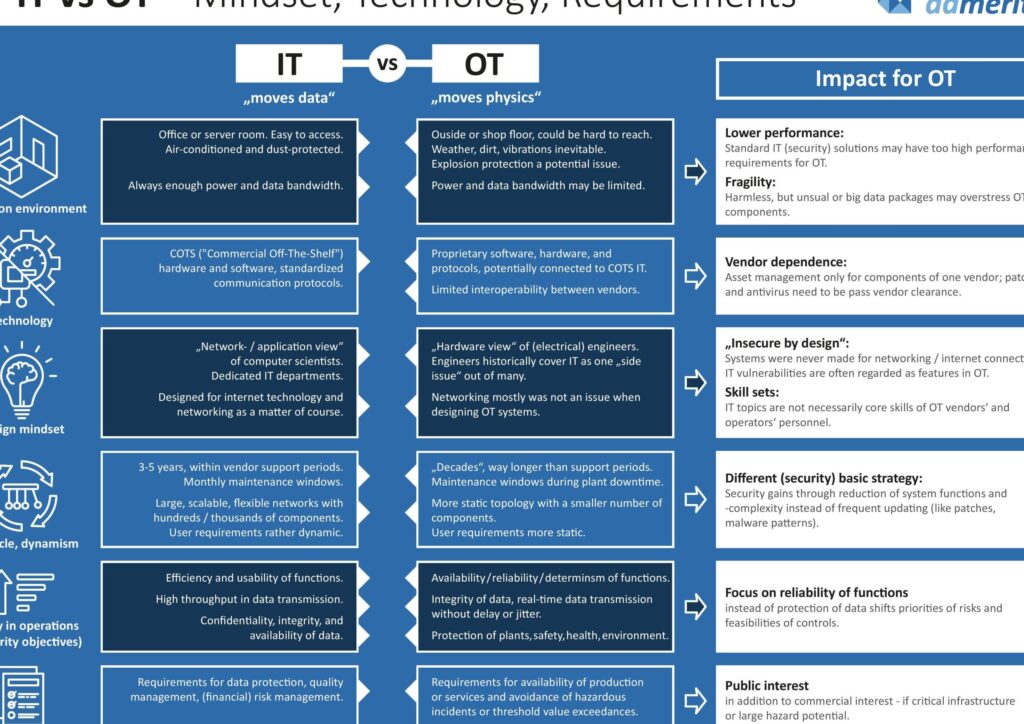
In today's digital landscape, security is a top priority for organizations. Two crucial aspects of security are Operational Technology (OT) and Information Technology (IT) security. While both are essential, they have distinct differences in their approach, goals, and best practices. OT security focuses on protecting industrial control systems and physical infrastructure, whereas IT security concentrates on safeguarding data and digital assets. Understanding these differences is vital to implementing effective security measures and ensuring the overall safety and reliability of an organization's operations and assets. Effective security strategies require a deep understanding of these differences.
Understanding the Distinction between Operational Technology (OT) and Information Technology (IT) Security
The realm of cybersecurity is vast and intricate, encompassing various domains, including Operational Technology (OT) and Information Technology (IT). While both are crucial for the smooth operation of modern organizations, they serve different purposes and face unique challenges. OT security focuses on protecting the hardware and software that control and monitor industrial processes, such as those found in manufacturing, energy, and transportation. On the other hand, IT security is concerned with safeguarding the integrity of data and the systems that process, store, and transmit this data. Understanding the distinctions between OT and IT security is essential for implementing effective security measures.
Historical Context of OT and IT Security
Historically, OT and IT systems have evolved separately, with OT focusing on reliability and availability, and IT emphasizing confidentiality, integrity, and availability. This separation has led to different security priorities and practices. OT systems, often considered critical infrastructure, demand high uptime and reliability, as downtime can have significant economic and safety implications. In contrast, IT systems have traditionally prioritized data protection against unauthorized access and breaches.
Key Differences in Threat Landscape
The threat landscapes for OT and IT differ significantly. OT systems are increasingly vulnerable to cyber-physical attacks that can have direct physical consequences, such as disrupting production or causing harm to personnel and the environment. IT systems, meanwhile, are more commonly targeted by phishing attacks, ransomware, and other forms of cybercrime aimed at stealing or compromising data. The attack vectors and motivations behind these threats vary, necessitating distinct security approaches.
Security Measures and Best Practices
Implementing robust security measures requires a deep understanding of the specific threats and vulnerabilities facing OT and IT systems. For OT, this includes network segmentation, secure remote access, and regular system updates. For IT, best practices encompass multi-factor authentication, encryption, and continuous monitoring for suspicious activity. Additionally, incident response plans should be in place for both domains to quickly respond to and mitigate the effects of a security breach.
Training and Awareness
Training and awareness are critical components of OT and IT security. Personnel operating and maintaining these systems must be educated on the potential risks and the security protocols in place to mitigate them. This includes understanding how to identify and report suspicious activity, the importance of password security, and the role of physical security in protecting access to OT and IT systems.
Integration and Convergence of OT and IT Security
As OT and IT systems become increasingly interconnected, there is a growing need for integration and convergence of their security practices. This involves adopting a holistic security approach that considers the entire organization's risk posture, rather than treating OT and IT security in isolation. By bridging the gap between these two domains, organizations can enhance their overall cyber resilience and better protect against the evolving threat landscape.
| Domain | Primary Focus | Key Security Concerns |
|---|---|---|
| OT Security | Protection of industrial processes and physical systems | Cyber-physical attacks, system reliability, and availability |
| IT Security | Protection of data and information systems | Data breaches, phishing, ransomware, and unauthorized access |
What is the difference between IT security and OT security?
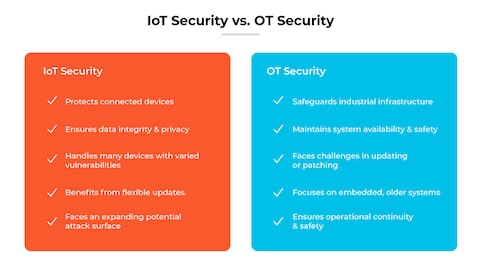
The main difference between IT security and OT security lies in their primary focus and the type of systems they protect. IT security focuses on protecting information technology systems, such as computers, networks, and data storage, from cyber threats and data breaches. On the other hand, OT security focuses on protecting operational technology systems, such as industrial control systems, SCADA systems, and IoT devices, from physical and cyber threats that could compromise the safety and reliability of these systems.
IT Security vs OT Security: Key Differences
The key differences between IT security and OT security are rooted in the distinct nature of the systems they protect. IT security is concerned with protecting digital assets, such as data and software, from cyber attacks and malware. In contrast, OT security is focused on protecting physical assets, such as industrial equipment and infrastructure, from physical and cyber threats that could cause equipment damage or disrupt operations. Some key differences include:
- System architecture: IT systems are often designed with security in mind, whereas OT systems are designed for reliability and availability.
- Threat landscape: IT systems face a wide range of cyber threats, including phishing and ransomware, whereas OT systems face physical and cyber threats, including equipment failure and sabotage.
- Security protocols: IT systems often employ firewalls and intrusion detection systems, whereas OT systems may employ access control and surveillance measures to prevent unauthorized access.
OT Security: Unique Challenges and Considerations
OT security presents unique challenges and considerations due to the critical infrastructure and industrial processes it supports. Operational technology systems are often legacy systems that were not designed with security in mind, making them vulnerable to cyber attacks and equipment failure. Additionally, OT systems often require real-time monitoring and control, making it essential to implement security measures that do not disrupt operations. Some key considerations include:
- System downtime: OT systems cannot afford downtime, making it essential to implement security measures that do not interrupt operations.
- Equipment safety: OT systems must ensure the safety of equipment and personnel, making it essential to implement security measures that prevent equipment damage or accidents.
- Regulatory compliance: OT systems must comply with regulations and standards, such as NERC CIP and ISA 99, which dictate security requirements for critical infrastructure.
Convergence of IT and OT Security: Benefits and Challenges
The convergence of IT and OT security presents both benefits and challenges. On the one hand, converging IT and OT security can provide greater visibility and control over security threats, allowing for more effective incident response. On the other hand, converging IT and OT security can also introduce new risks and complexities, such as integrating different security protocols and managing diverse security requirements. Some key benefits and challenges include:
- Improved visibility: Converging IT and OT security can provide greater visibility into security threats, allowing for more effective threat detection and incident response.
- Increased complexity: Converging IT and OT security can introduce new complexities, such as integrating different security protocols and managing diverse security requirements.
- Enhanced collaboration: Converging IT and OT security can foster greater collaboration between IT and OT teams, allowing for more effective security management and incident response.
How do IT and OT security practices and systems vary?

The main difference between IT and OT security practices and systems lies in their primary objectives. IT security focuses on protecting confidentiality, integrity, and availability of data, whereas OT security prioritizes safety, reliability, and efficiency of operational processes. This fundamental difference leads to distinct approaches in security practices and systems.
Network Architecture and Connectivity
IT and OT networks have distinct architectures and connectivity requirements. IT networks are designed for high-speed data transfer and flexibility, often using TCP/IP protocols. In contrast, OT networks prioritize real-time communication and deterministic behavior, frequently employing industrial protocols like Modbus or Profinet. Key differences in network architecture and connectivity include:
- Network segmentation: OT networks often require more stringent segmentation to prevent lateral movement of threats.
- Device management: OT devices, such as PLCs and RTOS, have unique management requirements compared to IT devices like servers and workstations.
- Communication protocols: OT networks use industry-specific protocols that may not be compatible with IT networks, requiring gateways or protocol converters for integration.
Security Threats and Risks
The threat landscape for IT and OT systems differs significantly. IT systems face cyber threats like malware, phishing, and DDoS attacks, which can be mitigated with firewalls, intrusion detection systems, and antivirus software. OT systems, on the other hand, are vulnerable to physical threats, equipment failures, and environmental factors, which can be addressed through redundancy, backup systems, and condition monitoring. Key differences in security threats and risks include:
- Threat vectors: OT systems are more susceptible to insider threats and physical attacks, while IT systems are more vulnerable to external threats and social engineering.
- Risk assessment: OT systems require hazard and operability studies (HAZOP) to identify potential risks, whereas IT systems rely on risk management frameworks like NIST or ISO 27001.
- Incident response: OT systems often have limited incident response capabilities due to limited network connectivity and lack of visibility, making it essential to develop customized incident response plans.
Compliance and Regulatory Frameworks
IT and OT systems are subject to different regulatory frameworks and compliance requirements. IT systems must adhere to data protection regulations like GDPR or HIPAA, while OT systems are governed by industry-specific regulations like IEC 62443 or NIST Cybersecurity Framework. Key differences in compliance and regulatory frameworks include:
- Standards and guidelines: OT systems are often subject to industry-specific standards like API or ISA, whereas IT systems follow general IT security standards like ISO 27001 or NIST SP 800-53.
- Compliance requirements: OT systems may require certification or validation to ensure functional safety and security, whereas IT systems typically require audits and risk assessments to demonstrate compliance.
- Regulatory bodies: OT systems are often regulated by industry-specific organizations like NFPA or API, while IT systems are overseen by general regulatory bodies like FTC or FCC.
What is the difference between OT and IT priorities?
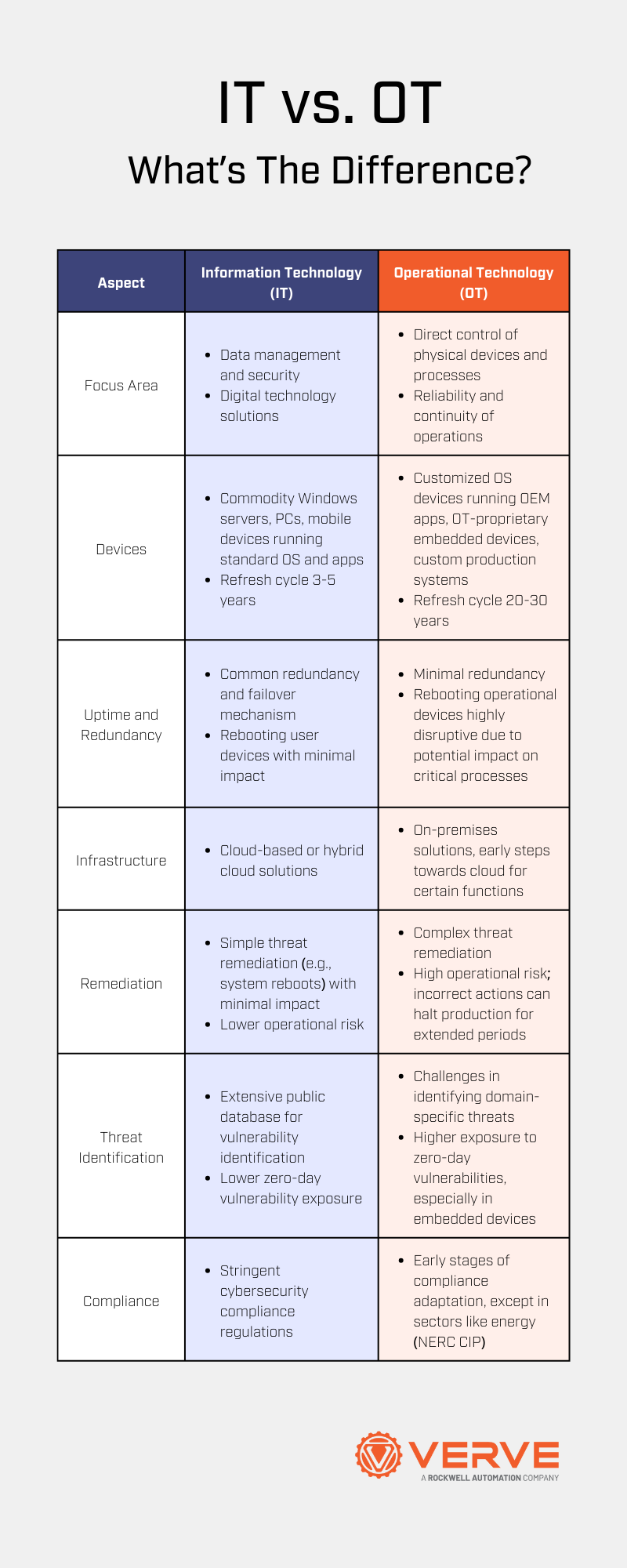
The main difference between Operational Technology (OT) and Information Technology (IT) priorities lies in their primary focus and goals. OT priorities are centered around Industrial Control Systems (ICS), which are used to monitor, control, and manage industrial processes, such as manufacturing, transportation, and energy production. On the other hand, IT priorities are focused on information systems, which are used to manage and process data, support business operations, and provide services to customers.
OT Priorities Focus on Industrial Control Systems
OT priorities are driven by the need to ensure the reliability, availability, and safety of industrial processes. This requires a focus on real-time monitoring, predictive maintenance, and incident response. Some key aspects of OT priorities include:
- Process control: Ensuring that industrial processes are running smoothly and efficiently
- Asset management: Managing and maintaining industrial equipment and assets
- Cybersecurity: Protecting OT systems from cyber threats and data breaches
IT Priorities Focus on Information Systems
IT priorities, on the other hand, are focused on information systems, which are used to support business operations and provide services to customers. IT priorities are driven by the need to ensure the availability, integrity, and confidentiality of data. Some key aspects of IT priorities include:
- Data management: Managing and processing large amounts of data to support business decision-making
- Network security: Protecting IT systems from cyber threats and data breaches
- User support: Providing technical support and training to users of IT systems
Convergence of OT and IT Priorities
In recent years, there has been a growing trend towards the convergence of OT and IT priorities, as industrial organizations increasingly rely on digital technologies to support their operations. This convergence requires a focus on interoperability, integration, and collaboration between OT and IT systems. Some key aspects of this convergence include:
- Data integration: Integrating data from OT and IT systems to support business decision-making
- Cybersecurity: Protecting converged OT and IT systems from cyber threats and data breaches
- Digital transformation: Leveraging digital technologies to transform industrial operations and improve efficiency and productivity
What are the three biggest security challenges end customers face in OT?

The three biggest security challenges end customers face in Operational Technology (OT) are complexity, connectivity, and vulnerability. OT systems are becoming increasingly interconnected, which creates a larger attack surface for potential threats. As a result, end customers must navigate these challenges to ensure the security and reliability of their OT systems.
Increased Complexity of OT Systems
The increasing complexity of OT systems is a significant security challenge for end customers. As OT systems become more interconnected and integrated with other systems, they become more difficult to manage and secure. This complexity can lead to configuration errors, incompatibility issues, and security vulnerabilities. Some of the key challenges associated with complex OT systems include:
- Lack of standardization: Different systems and devices may have different communication protocols and security standards, making it difficult to integrate and secure them.
- Inadequate training and support: End customers may not have the necessary skills and knowledge to manage and secure complex OT systems.
- Insufficient resources: End customers may not have the necessary budget and personnel to effectively manage and secure complex OT systems.
Growing Connectivity of OT Systems
The growing connectivity of OT systems is another significant security challenge for end customers. As OT systems become more connected to other systems and devices, they become more vulnerable to cyber threats. This connectivity can also create new attack vectors, such as unauthorized access and data breaches. Some of the key challenges associated with connected OT systems include:
- Increased attack surface: Connected OT systems provide more opportunities for hackers and malicious actors to launch attacks.
- Lack of visibility and control: End customers may not have real-time visibility into the security status of their connected OT systems.
- Inadequate security measures: End customers may not have sufficient security measures in place to protect their connected OT systems from cyber threats.
Vulnerability of OT Systems to Cyber Threats
The vulnerability of OT systems to cyber threats is a significant security challenge for end customers. OT systems are often unpatched and unsecured, making them easy targets for hackers and malicious actors. This vulnerability can lead to disruptions to critical infrastructure and loss of productivity. Some of the key challenges associated with vulnerable OT systems include:
- Lack of security awareness: End customers may not be aware of the potential risks and vulnerabilities of their OT systems.
- Inadequate security testing: End customers may not have regular security testing and vulnerability assessments in place to identify and remediate security vulnerabilities.
- Insufficient incident response planning: End customers may not have effective incident response plans in place to respond to security incidents and cyber attacks.
Frequently Asked Questions
What is the main difference between OT and IT security?
The main difference between Operational Technology (OT) and Information Technology (IT) security lies in their primary objectives and areas of focus. OT refers to the hardware and software used to control and monitor industrial processes, such as SCADA systems, ICS, and IoT devices, with the primary goal of ensuring the reliability, safety, and efficiency of these processes. On the other hand, IT security focuses on protecting confidentiality, integrity, and availability of data and information systems. While IT security is concerned with preventing cyber threats such as hacking, malware, and data breaches, OT security is focused on preventing physical harm to people, the environment, and equipment, as well as ensuring the continuity of industrial operations.
What are the key challenges in implementing OT security best practices?
Implementing OT security best practices can be challenging due to several factors, including the complexity of industrial control systems, the lack of standardization, and the limited resources available for cybersecurity. Additionally, OT systems often have long lifecycles, which can make it difficult to update or replace them with more secure versions. Furthermore, OT environments often require high availability and redundancy, which can make it challenging to implement security measures such as firewalls, intrusion detection systems, and patch management without disrupting critical operations. To overcome these challenges, organizations must adopt a risk-based approach to OT security, prioritizing the most critical assets and vulnerabilities, and implementing security controls that are tailored to the specific needs of their OT environment.
How can organizations ensure the security of their OT systems?
To ensure the security of their OT systems, organizations should implement a comprehensive OT security program that includes risk assessments, vulnerability management, incident response planning, and security awareness training. They should also implement technical security controls such as firewalls, intrusion detection systems, and access control to prevent unauthorized access to OT systems. Additionally, organizations should regularly update and patch their OT systems to fix known vulnerabilities, and implement segmentation and isolation to prevent the lateral movement of malicious actors. It is also essential to monitor OT systems in real-time to detect and respond to security incidents quickly, and to collaborate with IT and cybersecurity teams to ensure a unified approach to security.
What are the best practices for integrating OT and IT security?
To integrate OT and IT security effectively, organizations should adopt a converged approach that brings together OT and IT teams to share knowledge, expertise, and resources. This can be achieved by establishing a unified security governance framework that outlines policies, procedures, and standards for OT and IT security. Organizations should also implement common security controls and technologies that can be used across both OT and IT environments, such as identity and access management, incident response, and threat intelligence. Furthermore, organizations should regularly conduct risk assessments and vulnerability management activities to identify and mitigate risks that affect both OT and IT systems. By adopting these best practices, organizations can improve their overall security posture and reduce the risk of cyber threats to their OT and IT systems.
Leave a Reply