Top Data Breach Protection Strategies for Businesses

As technology advances, data breaches are becoming increasingly common, posing significant threats to businesses. A single breach can result in substantial financial losses, compromised customer trust, and damage to a company's reputation. With the rise of cyber attacks, it is essential for businesses to prioritize data protection. Implementing effective strategies can help prevent breaches and minimize their impact. This article will explore the top data breach protection strategies for businesses, providing valuable insights and practical tips to help organizations safeguard their sensitive information and maintain a secure online presence. Strong security measures are now a necessity.
Effective Data Breach Protection for Businesses: A Comprehensive Approach
Data breach protection is a critical aspect of modern business operations. As technology advances and more data is stored digitally, the risk of data breaches increases. Businesses must take proactive measures to protect their sensitive information from unauthorized access. This involves implementing a combination of security measures, employee training, and incident response plans.
Implementing Strong Access Controls
Implementing strong access controls is essential for preventing data breaches. This includes using multi-factor authentication, password management systems, and role-based access control. By limiting access to sensitive data, businesses can reduce the risk of unauthorized access. Additionally, regular security audits can help identify vulnerabilities and ensure that access controls are effective.
Conducting Regular Security Audits
Regular security audits are crucial for identifying vulnerabilities and ensuring the effectiveness of data breach protection strategies. These audits should include penetration testing, vulnerability assessments, and compliance checks. By conducting regular audits, businesses can identify areas for improvement and implement corrective measures to strengthen their security posture.
Developing an Incident Response Plan
Developing an incident response plan is critical for responding to data breaches effectively. This plan should include procedures for containment, eradication, recovery, and post-incident activities. By having a plan in place, businesses can minimize the impact of a data breach and ensure business continuity.
Training Employees on Data Security Best Practices
Training employees on data security best practices is essential for preventing data breaches. This includes educating employees on phishing attacks, social engineering tactics, and safe computing practices. By training employees, businesses can reduce the risk of human error and ensure that employees are security-aware.
Utilizing Advanced Security Technologies
Utilizing advanced security technologies is crucial for protecting against sophisticated threats. This includes using artificial intelligence, machine learning, and threat intelligence to detect and respond to potential threats. By leveraging these technologies, businesses can strengthen their security posture and stay ahead of emerging threats.
| Data Breach Protection Strategy | Description | Benefits |
|---|---|---|
| Implementing Strong Access Controls | Using multi-factor authentication, password management systems, and role-based access control | Reduces risk of unauthorized access, improves security posture |
| Conducting Regular Security Audits | Identifying vulnerabilities, ensuring compliance, and implementing corrective measures | Identifies areas for improvement, strengthens security posture |
| Developing an Incident Response Plan | Establishing procedures for containment, eradication, recovery, and post-incident activities | Minimizes impact of data breach, ensures business continuity |
| Training Employees on Data Security Best Practices | Education on phishing attacks, social engineering tactics, and safe computing practices | Reduces risk of human error, ensures employees are security-aware |
| Utilizing Advanced Security Technologies | Using artificial intelligence, machine learning, and threat intelligence to detect and respond to threats | Strengthens security posture, stays ahead of emerging threats |
How to protect your business from a data breach?
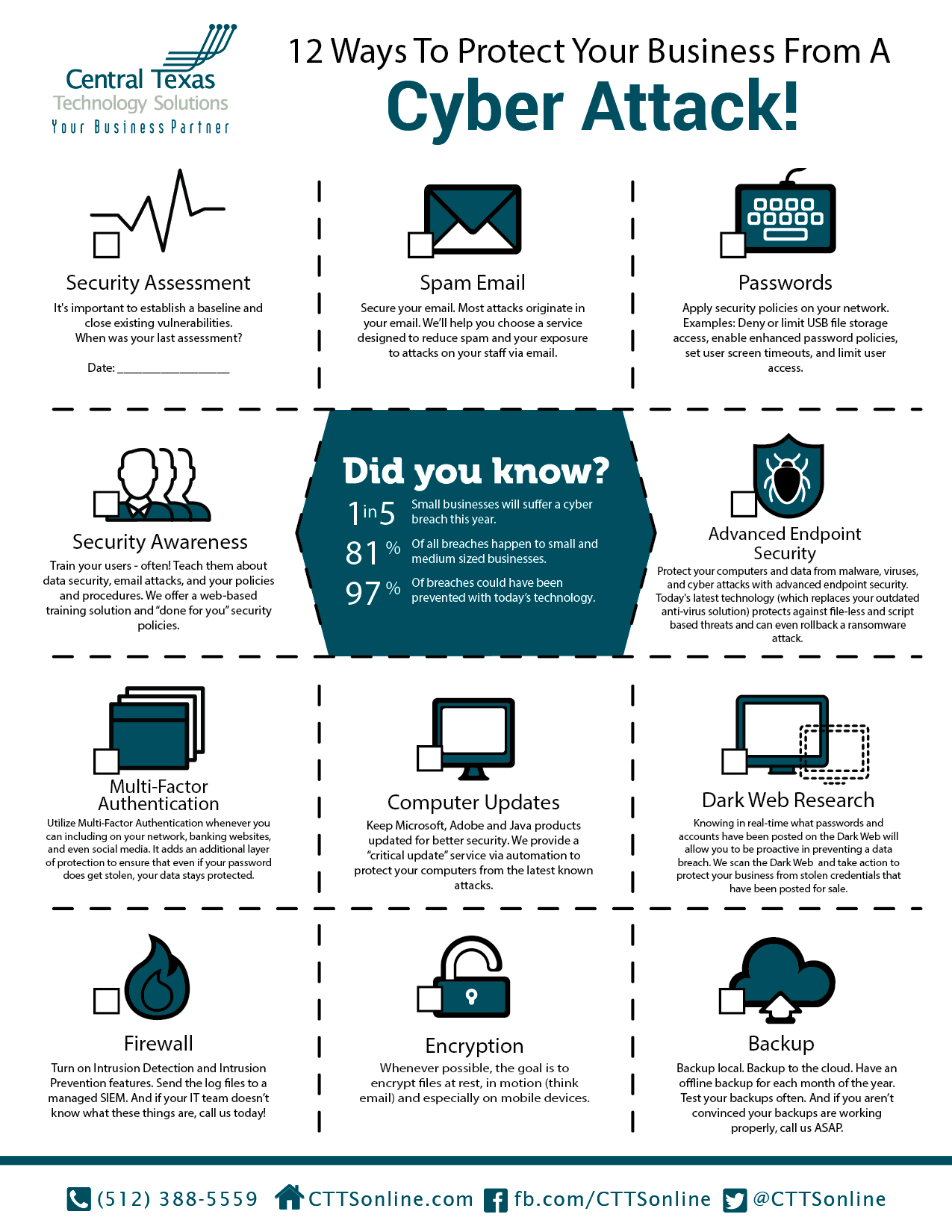
To protect your business from a data breach, it is essential to implement robust security measures. A data breach can have severe consequences, including financial loss, damage to your reputation, and legal liabilities. Therefore, it is crucial to take proactive steps to prevent such incidents. This can be achieved by conducting regular security audits, implementing firewalls, and using encryption to protect sensitive data.
Implementing Security Measures
To protect your business from a data breach, you need to implement robust security measures. This includes using strong passwords, implementing multi-factor authentication, and regularly updating your software and operating systems. Additionally, you should:
- Use anti-virus software to protect against malware and other online threats
- Implement a incident response plan to quickly respond to a data breach
- Provide security awareness training to your employees to prevent human error
By taking these steps, you can significantly reduce the risk of a data breach and protect your business from cyber threats.
Protecting Sensitive Data
Protecting sensitive data is critical to preventing a data breach. This includes customer information, financial data, and intellectual property. To protect this data, you should use encryption to make it unreadable to unauthorized parties. Additionally, you should:
- Use secure protocols for data transmission, such as HTTPS
- Implement access controls to limit who can access sensitive data
- Use data backup and recovery systems to ensure business continuity in the event of a breach
By protecting sensitive data, you can prevent identity theft, financial loss, and other consequences of a data breach.
Responding to a Data Breach
In the event of a data breach, it is essential to respond quickly and effectively. This includes notifying affected parties, containing the breach, and conducting a thorough investigation. Additionally, you should:
- Use incident response tools to quickly identify and contain the breach
- Provide support to affected parties, such as credit monitoring and identity theft protection
- Conduct a post-breach analysis to identify the cause of the breach and prevent future incidents
By responding quickly and effectively to a data breach, you can minimize the damage and reputation loss associated with a breach.
What are four proven data protection strategies a company can use to protect their data stored in the cloud?

To protect their data stored in the cloud, companies can use several proven data protection strategies. These strategies are designed to ensure the confidentiality, integrity, and availability of data. Four of these strategies include data encryption, access control, data backup, and cloud security monitoring.
Data Encryption Strategies
Data encryption is a crucial strategy for protecting data stored in the cloud. This involves converting data into a cipher that can only be deciphered with a decryption key. Companies can use symmetric or asymmetric encryption methods to protect their data. Some benefits of data encryption include:
- Protects data from unauthorized access
- Ensures confidentiality and integrity of data
- Meets regulatory requirements for data protection
Access Control and Authentication
Access control and authentication are essential strategies for protecting data stored in the cloud. This involves controlling who can access the data and ensuring that only authorized personnel can view or modify it. Companies can use multi-factor authentication and role-based access control to protect their data. Some benefits of access control and authentication include:
- Prevents unauthorized access to data
- Ensures that only authorized personnel can access data
- Provides a audit trail of all data access and modifications
Cloud Security Monitoring and Backup
Cloud security monitoring and backup are critical strategies for protecting data stored in the cloud. This involves monitoring the cloud environment for security threats and backing up data regularly to prevent data loss. Companies can use cloud security monitoring tools and data backup software to protect their data. Some benefits of cloud security monitoring and backup include:
- Provides real-time monitoring of the cloud environment
- Ensures business continuity in the event of a security breach
- Prevents data loss due to hardware failure or human error
What are the 5 steps of the data breach plan?

The data breach plan is a critical component of any organization's cybersecurity strategy. It outlines the steps to be taken in the event of a security incident to minimize the impact and protect sensitive information. The 5 steps of the data breach plan are:
1. Identification: Identifying the breach and assessing its severity.
2. Containment: Containing the breach to prevent further damage.
3. Eradication: Eradicating the root cause of the breach.
4. Recovery: Recovering from the breach and restoring systems.
5. Post-incident activities: Conducting post-incident activities to prevent future breaches.
Data Breach Plan Preparation
Preparation is key to responding effectively to a data breach. This involves developing a comprehensive plan that outlines the steps to be taken in the event of a breach. The plan should include clear roles and responsibilities for each team member, as well as established protocols for containing and eradicating the breach. Some important considerations for preparation include:
- Conducting regular risk assessments to identify potential vulnerabilities.
- Developing an incident response team to respond to breaches.
- Establishing communication channels to keep stakeholders informed.
Data Breach Response and Containment
The response to a data breach is critical to minimizing its impact. This involves quickly identifying the breach and taking steps to contain it. The goal of containment is to prevent further unauthorized access to sensitive information. Some key considerations for response and containment include:
- Activating the incident response team to respond to the breach.
- Isolating affected systems to prevent further damage.
- Conducting a thorough investigation to determine the cause of the breach.
Data Breach Recovery and Post-Incident Activities
Recovery from a data breach involves restoring systems and sensitive information to a secure state. This also includes conducting post-incident activities to prevent future breaches. Some important considerations for recovery and post-incident activities include:
- Restoring systems from backups to ensure business continuity.
- Conducting a thorough review of the breach to identify areas for improvement.
- Implementing additional security measures to prevent future breaches, such as multi-factor authentication and regular security audits.
What strategies would you recommend to mitigate the vulnerability and prevent data breaches?

To mitigate the vulnerability and prevent data breaches, it is essential to implement a combination of strategies that address the various aspects of cybersecurity. This includes network security, application security, and endpoint security. A comprehensive approach to security involves identifying vulnerabilities, assessing risks, and implementing controls to prevent or minimize the impact of a breach.
Implementing Security Measures
Implementing security measures is crucial to prevent data breaches. This includes encrypting sensitive data, using secure protocols for data transmission, and implementing access controls to ensure that only authorized personnel can access sensitive information. Some key strategies to implement include:
- Conducting regular security audits to identify vulnerabilities and assess risks
- Implementing a incident response plan to quickly respond to security incidents
- Providing ongoing security training to employees to ensure they are aware of the latest security threats and best practices
Using Technology to Prevent Breaches
Technology can play a significant role in preventing data breaches. This includes using firewalls to block unauthorized access to networks, implementing intrusion detection systems to detect and prevent malicious activity, and using encryption to protect sensitive data. Some key technologies to consider include:
- Advanced threat protection systems to detect and prevent sophisticated attacks
- Security information and event management systems to monitor and analyze security-related data
- Cloud security solutions to protect cloud-based data and applications
Developing a Culture of Security
Developing a culture of security is essential to preventing data breaches. This includes educating employees on the importance of security, promoting a culture of security awareness, and encouraging employees to report security incidents. Some key strategies to consider include:
- Establishing a security awareness program to educate employees on security best practices
- Recognizing and rewarding employees for their role in preventing security breaches
- Conducting regular security drills to ensure employees are prepared to respond to security incidents
Frequently Asked Questions
What are the most effective ways to prevent data breaches in businesses?
To prevent data breaches, businesses should implement multifactor authentication to ensure that only authorized personnel have access to sensitive information. Additionally, regular security audits should be conducted to identify vulnerabilities in the system and address them promptly. Employee education is also crucial, as many data breaches occur due to human error, such as clicking on phishing links or using weak passwords. By educating employees on best practices for data security, businesses can significantly reduce the risk of a data breach. Furthermore, incident response planning is essential to minimize the damage in case a breach occurs, and continuous monitoring of the system can help detect any suspicious activity.
How can businesses protect themselves against insider threats?
Businesses can protect themselves against insider threats by implementing access controls, such as role-based access and least privilege principles, to limit the amount of data that each employee can access. Monitoring user activity can also help detect any suspicious behavior, and background checks can be conducted on employees who will have access to sensitive information. Segregation of duties can also prevent any one employee from having too much control over sensitive data. Moreover, incident response planning should include procedures for responding to insider threats, and employee education should include training on reporting suspicious activity. By taking these steps, businesses can reduce the risk of insider threats and protect their sensitive data.
What role does encryption play in data breach protection?
Encryption plays a critical role in data breach protection, as it makes it difficult for unauthorized parties to read or access sensitive data, even if they manage to obtain it. Businesses should encrypt sensitive data both in transit and at rest, using strong encryption algorithms such as AES or RSA. Key management is also essential to ensure that encryption keys are securely stored and managed. Additionally, regular encryption audits should be conducted to ensure that encryption is properly implemented and up-to-date. By using encryption, businesses can protect their sensitive data from unauthorized access and reduce the risk of a data breach.
How can businesses ensure compliance with data breach regulations?
To ensure compliance with data breach regulations, businesses should stay up-to-date with the latest regulations, such as GDPR or HIPAA, and conduct regular compliance audits to ensure that they are meeting all requirements. Data breach notification procedures should be established to ensure that affected parties are notified in a timely manner in case of a breach. Compliance training should also be provided to employees to ensure that they understand their roles and responsibilities in maintaining compliance. Moreover, risk assessments should be conducted to identify potential vulnerabilities and address them promptly. By taking these steps, businesses can ensure compliance with data breach regulations and avoid fines and penalties.
Leave a Reply