Top OT Security Solutions to Protect Your Industrial Networks
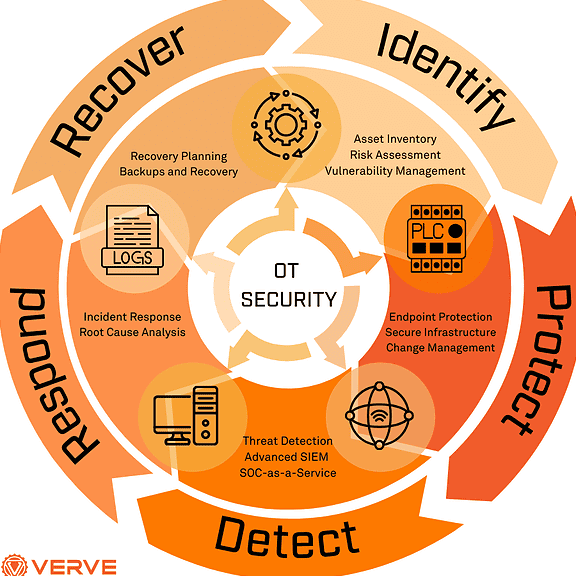
As the world becomes increasingly interconnected, industrial networks are facing growing threats from cyberattacks. Protecting these networks is crucial to prevent disruptions, data breaches, and potential harm to people and the environment. With the rise of Operational Technology (OT) security solutions, industries can now safeguard their systems and data from malicious activities. In this article, we will explore the top OT security solutions that can help protect industrial networks from cyber threats, ensuring the reliability, safety, and efficiency of critical infrastructure and operations. Effective protection requires a comprehensive approach.
Implementing Effective OT Security Measures to Safeguard Industrial Networks
To protect industrial networks from increasingly sophisticated cyber threats, it is essential to implement robust Operational Technology (OT) security solutions. OT security refers to the practice of protecting industrial control systems (ICS), supervisory control and data acquisition (SCADA) systems, and other critical infrastructure from cyber threats. Effective OT security measures can help prevent unauthorized access, data breaches, and system disruptions that can have significant consequences for industrial operations and national security.
Understanding OT Security Threats and Risks
OT security threats and risks are becoming increasingly complex and sophisticated. Industrial networks are vulnerable to cyber attacks, malware, and ransomware that can compromise system integrity and availability. To mitigate these risks, it is essential to understand the threat landscape and implement proactive security measures. This includes conducting regular security assessments, penetration testing, and vulnerability management to identify and address potential security weaknesses.
Implementing Firewalls and Network Segmentation
Implementing firewalls and network segmentation is a critical component of OT security. Firewalls can help block unauthorized access to industrial networks, while network segmentation can help isolate critical systems and prevent lateral movement in the event of a security breach. This can be achieved through the use of virtual local area networks (VLANs), access control lists (ACLs), and intrusion detection systems (IDS).
Using Encryption and Secure Communication Protocols
Using encryption and secure communication protocols is essential for protecting sensitive data transmitted over industrial networks. This includes implementing secure socket layer (SSL) or transport layer security (TLS) protocols to encrypt data in transit. Additionally, virtual private networks (VPNs) can be used to securely connect remote devices and systems to industrial networks.
Conducting Regular Security Audits and Training
Conducting regular security audits and training is crucial for maintaining the security posture of industrial networks. Security audits can help identify vulnerabilities and weaknesses, while training can help ensure that personnel are aware of security best practices and procedures. This includes providing regular security awareness training and incident response training to ensure that personnel are prepared to respond to security incidents.
Utilizing Advanced Threat Detection and Response Solutions
Utilizing advanced threat detection and response solutions is essential for detecting and responding to sophisticated cyber threats. This includes implementing artificial intelligence (AI) and machine learning (ML) based security solutions that can help detect anomalous behavior and predictive threats. Additionally, incident response plans and playbooks can be used to quickly respond to security incidents and minimize downtime.
| OT Security Solution | Description | Benefits |
|---|---|---|
| Firewalls | Network security system that monitors and controls incoming and outgoing network traffic | Prevents unauthorized access, blocks malicious traffic |
| Network Segmentation | Divides network into smaller, isolated segments to improve security and reduce lateral movement | Improves security posture, reduces attack surface |
| Encryption | Converts plaintext data into unreadable ciphertext to protect sensitive data | Protects data in transit, prevents eavesdropping and tampering |
| Security Audits | Comprehensive evaluation of network security to identify vulnerabilities and weaknesses | Identifies security risks, provides recommendations for improvement |
| Advanced Threat Detection | Uses AI and ML to detect and respond to sophisticated cyber threats | Detects anomalous behavior, predicts threats, improves incident response |
How to secure an OT network?

Securing an Operational Technology (OT) network is crucial to prevent cyber threats and data breaches. OT networks are used to monitor and control industrial processes, such as manufacturing, transportation, and energy production. To secure an OT network, it is essential to implement strong security measures to protect against malicious attacks.
Implementing Network Segmentation
Implementing network segmentation is a critical step in securing an OT network. This involves dividing the network into smaller, isolated segments to prevent lateral movement in case of a security breach. By segmenting the network, sensitive data and critical systems can be isolated from the rest of the network, reducing the risk of unauthorized access. Some key steps to implement network segmentation include:
- Identifying critical assets and sensitive data that need to be protected
- Dividing the network into isolated segments based on functional requirements
- Implementing firewalls and access controls to restrict network traffic between segments
Conducting Regular Security Audits
Conducting regular security audits is essential to identify vulnerabilities and weaknesses in the OT network. These audits should include penetration testing, vulnerability assessments, and configuration reviews to identify security gaps. By conducting regular security audits, security risks can be identified and mitigated, reducing the risk of cyber attacks. Some key steps to conduct regular security audits include:
- Identifying security risks and vulnerabilities in the OT network
- Conducting penetration testing and vulnerability assessments to identify security gaps
- Implementing remediation plans to address identified vulnerabilities
Implementing Incident Response Planning
Implementing incident response planning is critical to respond to security incidents in the OT network. This involves developing a comprehensive incident response plan that outlines incident response procedures, communication protocols, and remediation strategies. By having a well-planned incident response plan, security incidents can be responded to quickly and effectively, minimizing downtime and data loss. Some key steps to implement incident response planning include:
- Developing a comprehensive incident response plan that outlines incident response procedures
- Establishing incident response teams and communication protocols
- Conducting regular incident response training and exercises to ensure preparedness
What is the best protection for network security?
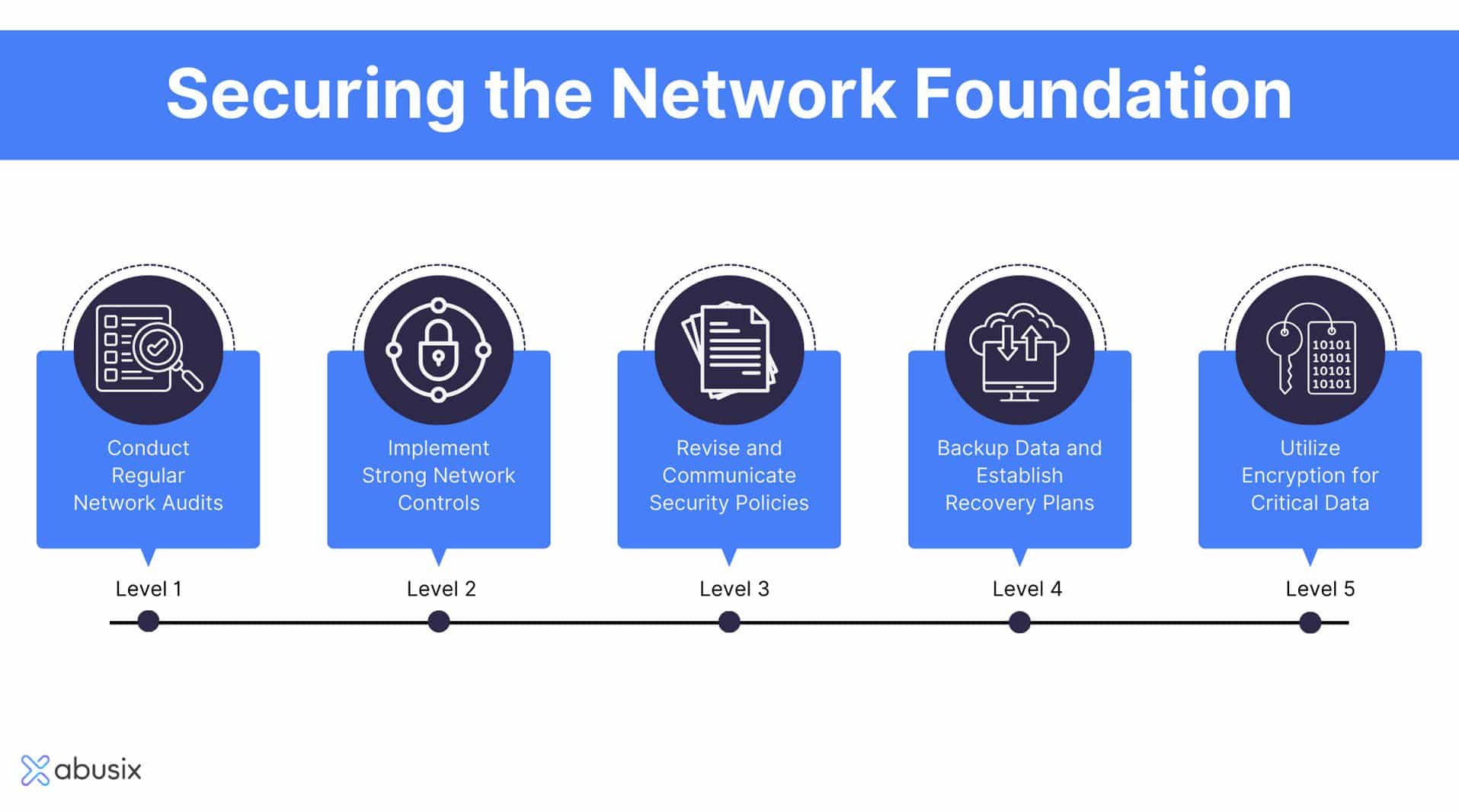
The best protection for network security is a combination of different measures that work together to prevent cyber threats and protect sensitive information. This includes implementing firewalls, intrusion detection systems, and encryption to secure data in transit and at rest. Additionally, network segmentation and access control can help to limit the spread of malware and prevent unauthorized access to sensitive areas of the network.
Network Security Measures
To protect a network from cyber attacks, several measures can be taken, including:
- Implementing firewalls to block unauthorized access to the network
- Using intrusion detection systems to identify and respond to potential security threats
- Conducting regular security audits to identify vulnerabilities and weaknesses in the network
These measures can help to prevent data breaches and protect sensitive information from being compromised.
Types of Network Security Threats
There are several types of network security threats that can compromise the integrity of a network, including:
- Malware, such as viruses, worms, and Trojans, which can damage or destroy data
- Phishing attacks, which can trick users into revealing sensitive information
- Denial of Service (DoS) attacks, which can overwhelm the network and make it unavailable
Understanding these types of threats is crucial to implementing effective network security measures.
Best Practices for Network Security
To ensure the security of a network, several best practices can be followed, including:
- Implementing strong passwords and multi-factor authentication to prevent unauthorized access
- Keeping software and operating systems up to date with the latest security patches
- Using encryption to protect sensitive data in transit and at rest
By following these best practices, organizations can help to protect their networks from cyber threats and ensure the security and integrity of their data.
What are the examples of OT security?
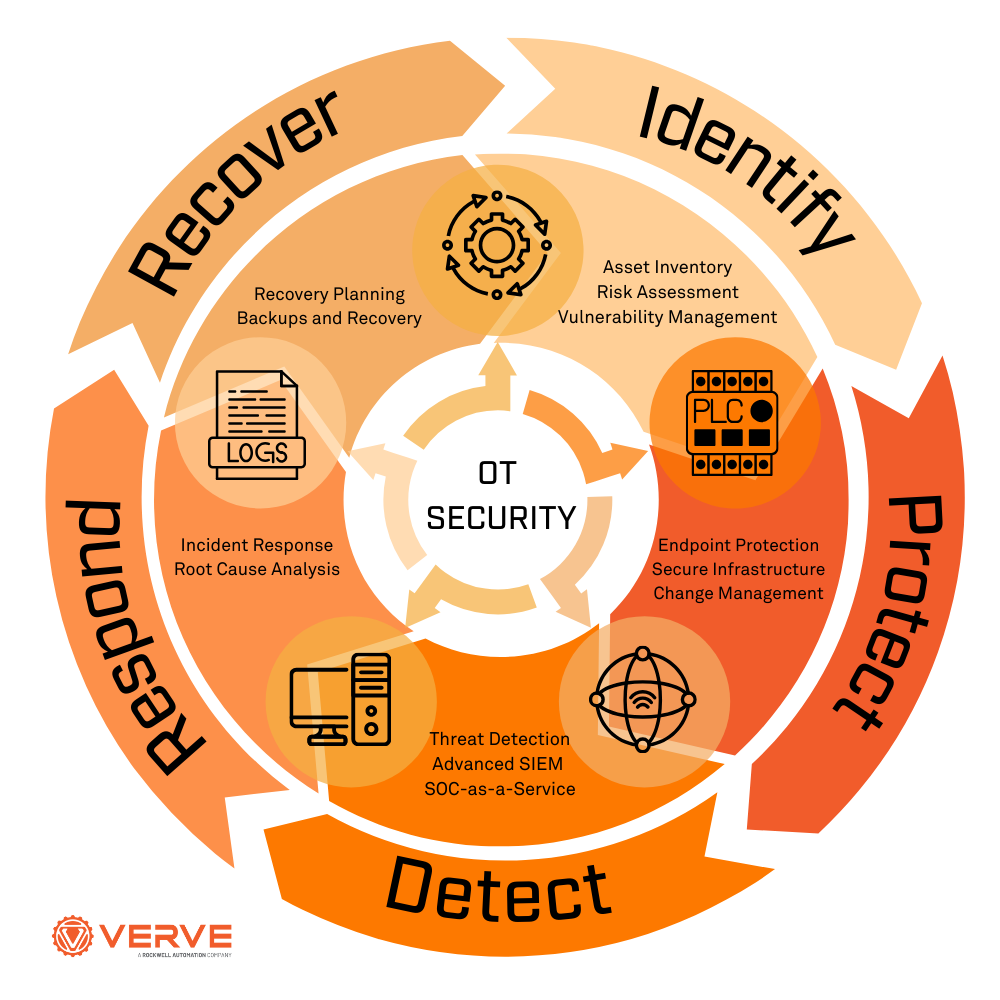
The examples of OT security include various measures to protect operational technology systems from cyber threats. These systems are used to monitor, control, and manage industrial processes, and their security is crucial to prevent disruptions and damage. OT security involves implementing security protocols, firewalls, and intrusion detection systems to prevent unauthorized access and malicious activity.
OT Security in Industrial Control Systems
OT security in industrial control systems is critical to prevent cyber attacks that can compromise the safety and reliability of these systems. Some examples of OT security measures in industrial control systems include:
- Implementing access control measures to restrict access to authorized personnel
- Using encryption to protect data transmitted between systems
- Conducting regular security audits to identify and address vulnerabilities
These measures help to prevent unauthorized access and malicious activity that can compromise the integrity of industrial control systems.
OT Security in Transportation Systems
OT security in transportation systems is essential to prevent disruptions and accidents. Some examples of OT security measures in transportation systems include:
- Implementing secure communication protocols to protect data transmitted between systems
- Using intrusion detection systems to detect and prevent cyber attacks
- Conducting regular security training for personnel to ensure they are aware of security threats and best practices
These measures help to prevent cyber attacks that can compromise the safety and reliability of transportation systems.
OT Security in Energy and Utilities
OT security in energy and utilities is critical to prevent disruptions and damage to the grid. Some examples of OT security measures in energy and utilities include:
- Implementing secure _SCADA_ systems to monitor and control the grid
- Using firewalls to prevent unauthorized access to systems
- Conducting regular security assessments to identify and address vulnerabilities
These measures help to prevent cyber attacks that can compromise the reliability and safety of energy and utilities systems.
What security measures are used to protect networks?
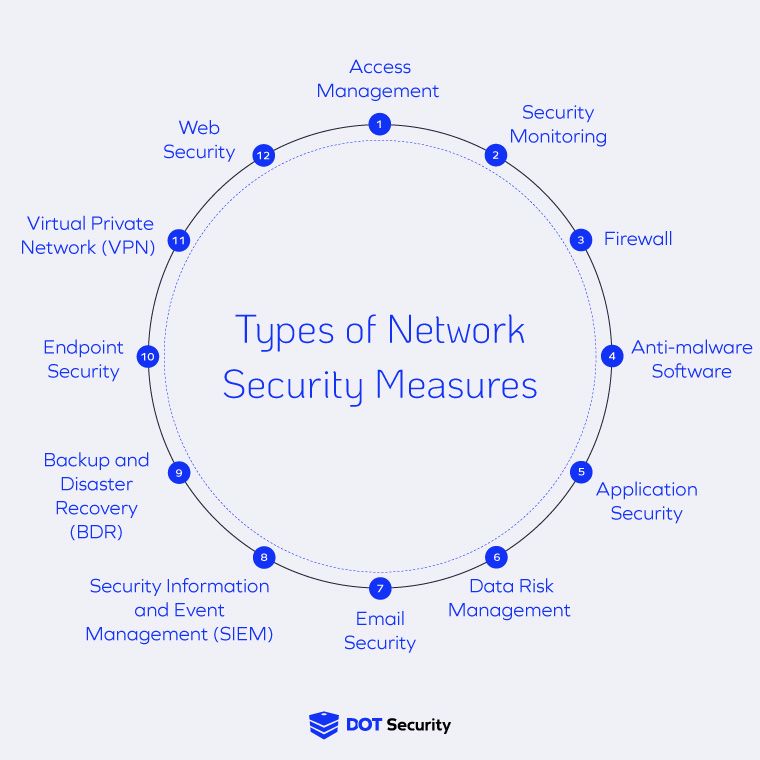
To protect networks, various security measures are implemented to prevent unauthorized access, use, disclosure, disruption, modification, or destruction of network resources. These measures include firewalls, intrusion detection systems, and encryption protocols to ensure the confidentiality, integrity, and availability of network data. Network security measures are designed to protect against cyber threats, such as hacking, malware, and denial-of-service attacks.
Network Access Control
Network access control is a crucial security measure used to protect networks. This involves implementing access control lists and authentication protocols to ensure that only authorized users and devices can access the network. Some common network access control measures include:
- Username and password authentication to verify the identity of users
- Multi-factor authentication to provide an additional layer of security
- Role-based access control to limit access to network resources based on user roles
Network Monitoring and Incident Response
Network monitoring and incident response are critical security measures used to protect networks. This involves monitoring network activity to detect and respond to security incidents in real-time. Some common network monitoring and incident response measures include:
- Intrusion detection systems to detect and alert on potential security threats
- Log analysis to identify and investigate security incidents
- Incident response planning to respond quickly and effectively to security incidents
Cryptography and Encryption
Cryptography and encryption are essential security measures used to protect networks. This involves using encryption protocols to protect data in transit and at rest. Some common cryptography and encryption measures include:
- Secure Sockets Layer/Transport Layer Security (SSL/TLS) to encrypt data in transit
- Virtual Private Networks (VPNs) to encrypt data transmitted over public networks
- Data encryption to protect data stored on network devices and servers
Frequently Asked Questions
What are the most effective Top OT Security Solutions for industrial networks?
The most effective Top OT Security Solutions for industrial networks involve a combination of network segmentation, firewall configurations, and intrusion detection systems. These solutions help to prevent unauthorized access and malicious activity by segregating the network into separate segments, each with its own set of access controls and security protocols. Additionally, incident response plans and continuous monitoring are essential to quickly identify and respond to potential security threats. By implementing these solutions, industrial networks can significantly reduce the risk of cyber attacks and protect their critical infrastructure.
How do Top OT Security Solutions protect against industrial cyber threats?
Top OT Security Solutions protect against industrial cyber threats by providing a layered defense approach that includes network monitoring, threat detection, and incident response. These solutions utilize advanced technologies such as artificial intelligence and machine learning to identify and analyze potential threats in real-time. By leveraging threat intelligence and anomaly detection, Top OT Security Solutions can quickly detect and respond to malicious activity, preventing damage to industrial control systems and protecting against data breaches. Furthermore, these solutions provide visibility into network activity, allowing for proactive measures to be taken to prevent cyber attacks.
What are the benefits of implementing Top OT Security Solutions in industrial networks?
The benefits of implementing Top OT Security Solutions in industrial networks include improved security posture, reduced risk of cyber attacks, and increased compliance with regulatory requirements. By implementing these solutions, industrial networks can protect their critical infrastructure and prevent disruptions to operations. Additionally, Top OT Security Solutions can help to reduce downtime and minimize the impact of a security breach. These solutions also provide visibility into network activity, allowing for data-driven decisions to be made to optimize security controls and improve overall network security.
How can industrial organizations choose the best Top OT Security Solution for their needs?
Industrial organizations can choose the best Top OT Security Solution for their needs by assessing their specific security requirements and evaluating the features and capabilities of different solutions. It is essential to consider factors such as network architecture, device compatibility, and scalability when selecting a Top OT Security Solution. Additionally, organizations should look for solutions that provide real-time monitoring, advanced threat detection, and incident response capabilities. By conducting thorough research and evaluating different options, industrial organizations can select the best Top OT Security Solution to protect their industrial networks and prevent cyber threats.
Leave a Reply